Elevate Your Security Posture with Managed Detection and Response
Transform your cybersecurity strategy with 24/7 AI-powered threat detection, rapid incident response, and expert security analysts protecting your business around the clock.
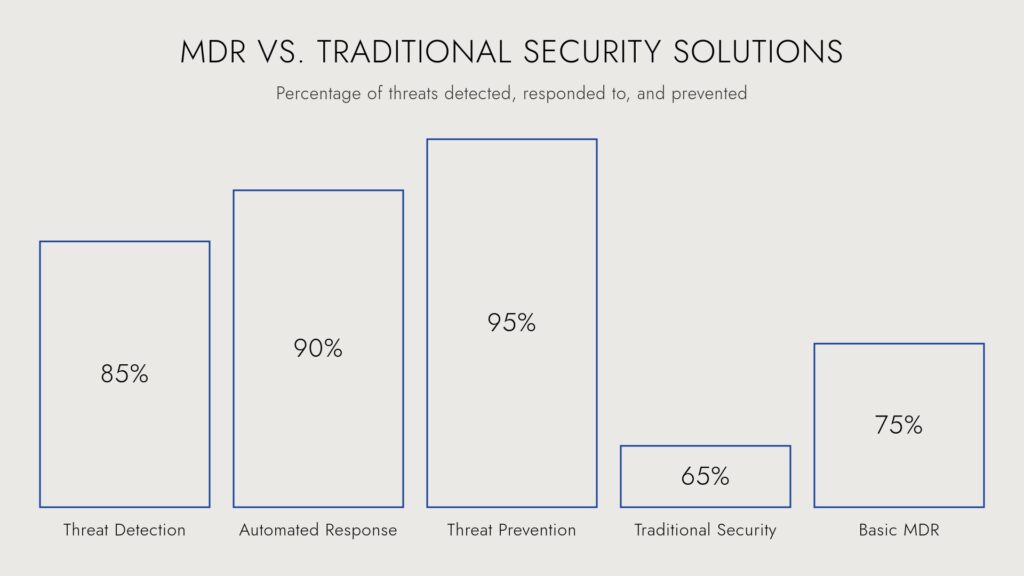
Every 39 seconds, a cyberattack occurs somewhere in the world. With businesses increasingly reliant on digital infrastructure, cybercriminals have more opportunities than ever to infiltrate networks, steal sensitive data, and disrupt operations. In 2023 alone, the average cost of a data breach reached $4.45 million, a 15% increase over the past three years.
Traditional security measures like firewalls and antivirus software are no longer enough to combat today’s sophisticated threats. Organizations need a proactive, intelligence-driven approach that not only detects threats in real-time but responds instantly before damage occurs. That’s where Managed Detection and Response (MDR) transforms your security posture.
The Evolving Cybersecurity Threat Landscape

Businesses face an unprecedented array of cyber threats that are growing in both sophistication and frequency:
Top Cybersecurity Threats Businesses Face Today
- Ransomware Attacks: Cybercriminals encrypt critical business data and demand ransom payments to restore access. High-profile attacks have crippled industries from healthcare to finance.
- Phishing & Social Engineering: Attackers use deceptive emails and messages to trick employees into revealing login credentials, often leading to massive data breaches.
- Supply Chain Attacks: Hackers compromise trusted vendors or software providers to gain access to a company’s network, as seen in high-profile breaches like SolarWinds.
- Advanced Persistent Threats (APTs): Sophisticated cybercriminal groups quietly infiltrate networks, remaining undetected for months while stealing valuable information.
💡 Key Insight: Traditional security measures are reactive, not proactive. They often detect threats after they’ve already infiltrated the network, leaving businesses scrambling to contain the damage.
Why Traditional Security Falls Short
Many organizations rely on traditional security tools like firewalls, antivirus software, and endpoint protection to guard against cyber threats. While these measures play a role in defense, they lack the agility, visibility, and proactive response needed to combat today’s sophisticated attacks.
The Limitations of Traditional Security
- Reactive, Not Proactive – Traditional security solutions often detect threats after they’ve already infiltrated the network, leaving businesses scrambling to contain the damage.
- Alert Fatigue & False Positives – Security teams are bombarded with alerts, many of which turn out to be false positives. This overload leads to critical threats being overlooked.
- Lack of 24/7 Monitoring – Cybercriminals don’t operate on a 9-to-5 schedule. Without round-the-clock surveillance, businesses are vulnerable to attacks that go unnoticed outside of working hours.
- Resource Constraints – Maintaining an in-house Security Operations Center (SOC) with skilled analysts, cutting-edge threat intelligence, and rapid response capabilities is costly and complex.
- Evolving Threats Bypass Legacy Defenses – Cybercriminals use AI-driven attacks, zero-day exploits, and advanced persistent threats (APTs) that can bypass traditional security tools.
The Need for a Smarter, Stronger Security Solution
Modern threats demand modern security solutions. Organizations need a cybersecurity approach that:
- ✅ Detects and responds to threats in real-time – not after an attack has already succeeded
- ✅ Leverages AI and expert human analysis to reduce false positives and identify real threats faster
- ✅ Provides 24/7 monitoring and response to ensure attacks are stopped immediately
- ✅ Integrates with existing security tools to enhance overall protection without disrupting business operations
This is exactly what Managed Detection and Response (MDR) delivers.
How Managed Detection and Response (MDR) Transforms Your Security
To effectively combat today’s relentless cyber threats, businesses need more than just detection—they need action. Managed Detection and Response (MDR) is a fully managed security service that combines AI-driven threat detection, expert human analysis, and rapid incident response to stop cyberattacks before they cause damage.
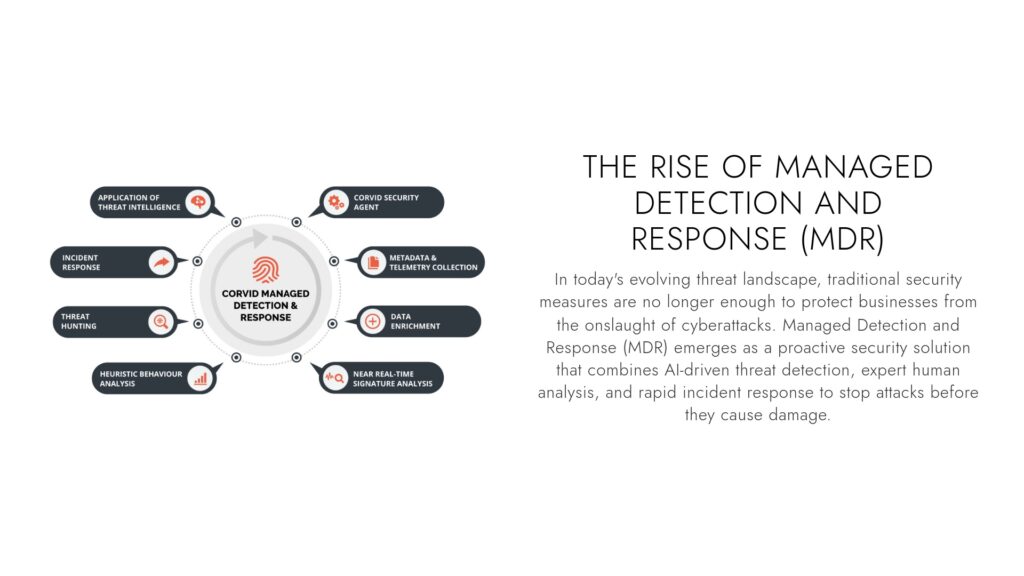
What is MDR?
Managed Detection and Response (MDR) is a proactive cybersecurity solution that offers:
- 🔹 24/7 monitoring & threat detection – Ensuring no attack goes unnoticed
- 🔹 Proactive threat hunting – Security experts actively search for hidden threats in your network
- 🔹 Rapid incident response – Cyber threats are neutralized in real time to prevent breaches
- 🔹 Advanced threat intelligence – MDR leverages global security data to stay ahead of attackers
- 🔹 Seamless integration – Works alongside your existing security stack for enhanced protection
Unlike traditional security tools that rely solely on automated detection, MDR combines AI-powered analytics with skilled security analysts, ensuring that even the most sophisticated cyber threats are identified and stopped before they can cause harm.
Case Study: How MDR Stopped a Targeted Phishing Attack

A mid-sized financial services firm was repeatedly hit with phishing attacks, despite having email security filters in place. Attackers managed to bypass defenses and gained access to a third-party vendor account.
By implementing an MDR solution, the company:
- ✅ Detected and blocked malicious login attempts in real-time
- ✅ Traced the attack back to a compromised supply chain vendor
- ✅ Stopped unauthorized access before any data was stolen
- ✅ Strengthened security controls to prevent future attacks
🚨 The Power of MDR: It doesn’t just detect threats—it actively stops them before damage occurs, reducing the average breach cost from $4.45 million to virtually zero.
Key Benefits of MDR Implementation
In today’s threat landscape, relying on traditional security solutions is no longer enough. Managed Detection and Response (MDR) offers a holistic, proactive approach to cybersecurity, ensuring that organizations stay ahead of attacks rather than reacting to them.
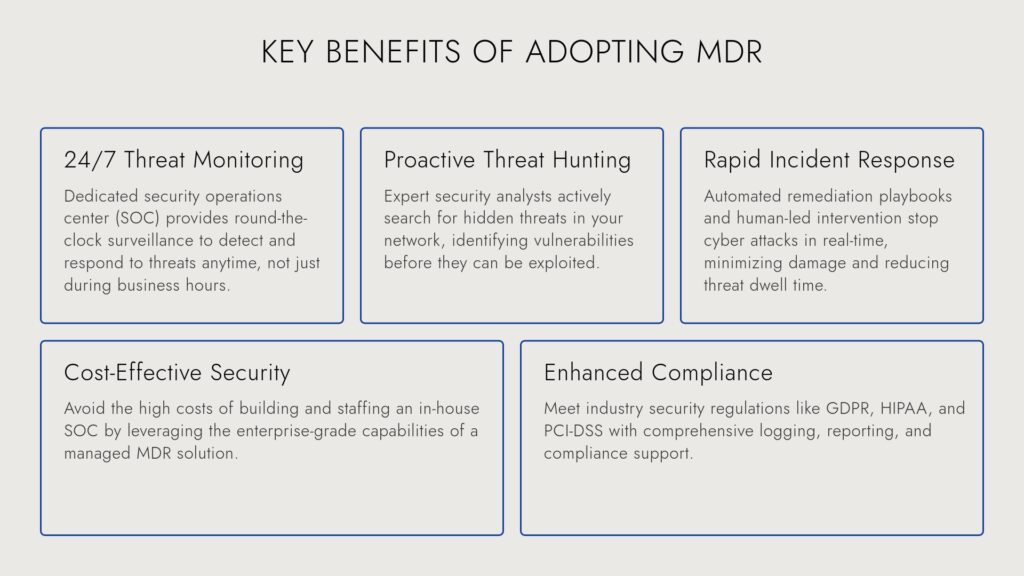
1. 24/7 Threat Monitoring & Proactive Threat Hunting
- 🔹 Always on, always watching – Cyber threats don’t wait for business hours, and neither does MDR. A dedicated Security Operations Center (SOC) provides round-the-clock surveillance to detect and neutralize threats before they escalate.
- 🔹 Proactive, not just reactive – MDR security analysts don’t just respond to alerts—they actively hunt for hidden threats in your environment, identifying vulnerabilities before attackers can exploit them.
2. Rapid Incident Detection & Response
- 🔹 Stop breaches before they spread – MDR doesn’t just identify threats; it takes action to contain and neutralize them in real-time.
- 🔹 Reduce dwell time – The longer a threat lingers undetected, the greater the damage. MDR drastically cuts threat dwell time, minimizing potential harm to your business.
3. Cost-Effective Security Without the Overhead
- 🔹 Eliminate the need for an in-house SOC – Hiring and maintaining a 24/7 security team is expensive and resource-intensive. MDR provides enterprise-level protection at a fraction of the cost.
- 🔹 Lower breach-related costs – Data breaches are costly, with an average financial impact of $4.45 million. MDR helps businesses avoid these catastrophic losses by stopping attacks before they succeed.
4. Advanced Threat Intelligence & AI-Driven Security
- 🔹 Stay ahead of evolving cyber threats – MDR leverages global threat intelligence to identify emerging attack patterns and automatically strengthen defenses.
- 🔹 AI-powered detection & response – Cutting-edge machine learning and behavioral analytics ensure that even the most sophisticated threats—like zero-day attacks and advanced persistent threats (APTs)—are detected and neutralized instantly.
5. Enhanced Compliance & Regulatory Readiness
- 🔹 Meet industry security requirements – Whether your business operates in finance, healthcare, SaaS, or e-commerce, MDR helps you stay compliant with GDPR, HIPAA, PCI-DSS, and other regulations.
- 🔹 Audit-ready security reports – With comprehensive logging, reporting, and compliance automation, MDR makes security audits fast and hassle-free.
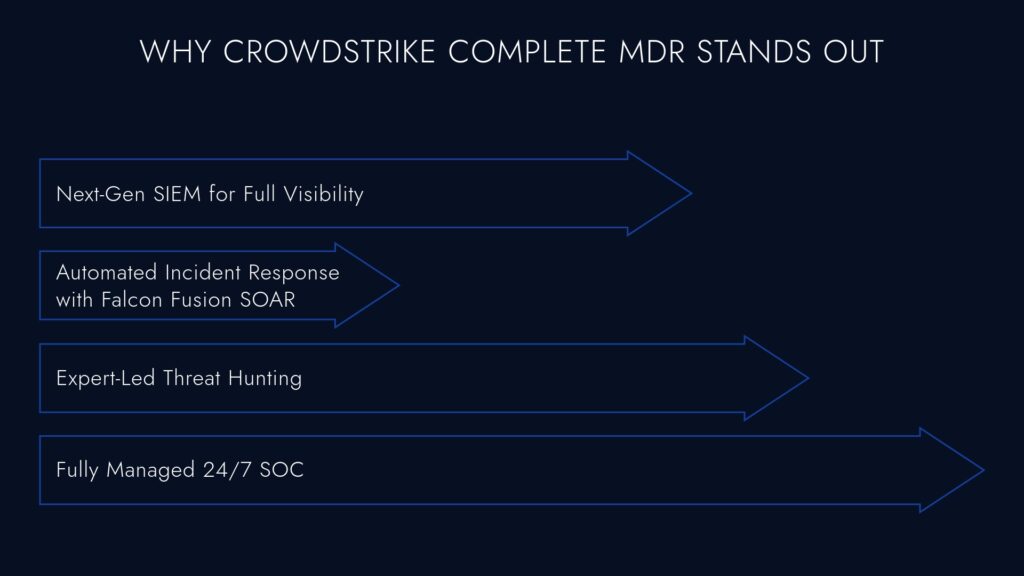
Why CrowdStrike Complete MDR Stands Above the Rest
With multiple MDR providers in the market, choosing the right solution can be overwhelming. While many offer basic monitoring and alerting, CrowdStrike Complete MDR delivers a fully managed, next-gen security experience—acting as your full-service Security Operations Center (SOC).
What Sets CrowdStrike Complete MDR Apart?
- ✅ Next-Gen SIEM for Complete Visibility – Unlike basic MDR services that focus only on endpoints, CrowdStrike integrates Next-Gen SIEM to monitor threats across your entire IT environment, including cloud, network, and identity-based attacks.
- ✅ Falcon Fusion SOAR for Automated Response – Stop threats instantly with automated remediation playbooks, reducing response times from hours to seconds.
- ✅ Expert-Led Threat Hunting – CrowdStrike’s elite security analysts actively hunt for hidden threats, ensuring no attack goes undetected.
- ✅ Full-Service SOC Without the Overhead – Get the power of a 24/7 security operations center without the costs of building and staffing one yourself.
🎯 Learn More: Discover why CrowdStrike Complete MDR is the future of security and how it can transform your organization’s cybersecurity posture.
Elevate Your IT Efficiency with Expert Solutions
Transform Your Technology, Propel Your Business
Ready to strengthen your security posture with managed detection and response? InventiveHQ specializes in implementing comprehensive MDR solutions that protect your business from evolving cyber threats. Our expert team delivers 24/7 monitoring, rapid incident response, and proactive threat hunting to keep your organization secure.


