Protocols enable different devices and software to communicate reliably.
Common protocols
- HTTP/HTTPS: Web browsing (port 80/443).
- FTP/SFTP: File transfers (port 21/22).
- SMTP/POP3/IMAP: Email (ports 25/110/143).
- DNS: Domain name resolution (port 53).
- SSH: Secure remote access (port 22).
- TCP/UDP: Transport layer protocols.
- IP: Internet layer addressing.
Protocol layers (OSI model)
- Physical: Cables, signals.
- Data Link: MAC addresses, switches.
- Network: IP addresses, routing.
- Transport: TCP/UDP, ports.
- Session: Connection management.
- Presentation: Data formatting, encryption.
- Application: HTTP, FTP, SMTP.
Security considerations
- Many protocols are unencrypted (use secure alternatives).
- Port scanning reveals running services.
- Protocol vulnerabilities enable attacks.
- Firewalls filter by protocol and port.
Related Articles
View all articles
10 Backup & Ransomware Questions Every IT Leader Must Ask
Ransomware attacks are no longer a matter ofif, butwhen. Is your backup strategy ready for the challenge?
Read article →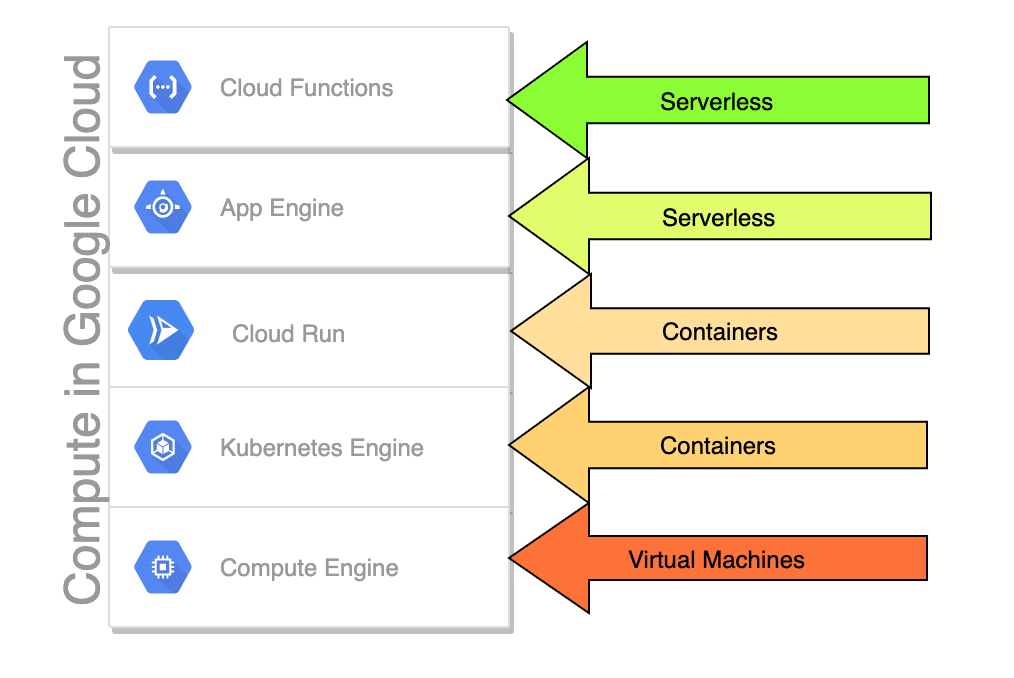
Comparing 5 Kinds of Compute on Google Cloud
When you think of compute, your mind probably goes straight to virtual machines. But there are actually at least 5 different kinds of compute on Google Cloud.
Read article →Disaster Recovery Testing & Validation Workflow | Complete
Master disaster recovery testing with this comprehensive 8-stage workflow guide. Learn RTO/RPO validation, failover testing, backup verification, and business continuity protocols using industry frameworks and proven methodologies.
Read article →SOC 2 Readiness & Audit Preparation Workflow | Complete
Complete SOC 2 readiness and audit preparation workflow for SaaS companies. Covers Trust Service Criteria selection, gap assessment, control implementation, evidence collection, Type I vs Type II decisions, and cost estimates for first-time certification.
Read article →Explore More Networking
View all termsBGP (Border Gateway Protocol)
The routing protocol that exchanges network reachability information between autonomous systems, forming the backbone of Internet routing.
Read more →DNSSEC (DNS Security Extensions)
A suite of specifications that add cryptographic authentication to DNS responses, preventing DNS spoofing and cache poisoning attacks.
Read more →Domain Name System (DNS)
The hierarchical naming system that translates human-readable domain names into IP addresses.
Read more →IP Address Geolocation
The process of determining the geographic location of an internet-connected device using its IP address.
Read more →MAC Address
A unique hardware identifier assigned to network interfaces for local network communication.
Read more →MX Record
A DNS record type that specifies which mail servers are responsible for receiving email for a domain.
Read more →