Cybersecurity Insights & Expert Guidance
Stay ahead of evolving threats with actionable cybersecurity insights, real-world case studies, and expert guidance from Inventive HQ's security team.
Featured Series
JSON Formatter & Validator
Format, validate, and beautify JSON with syntax highlighting, error detection, and tree view
Legal Cybersecurity
Navigate state bar regulations, protect attorney-client privilege, and build client trust with cybersecurity solutions designed specifically for law firms and legal service providers.

LP-Yelp-Cybersecurity
🔒 FREE Cybersecurity Consultation
Kubernetes Security & Hardening Workflow | CIS Benchmark
Master the complete Kubernetes security workflow from CIS benchmark assessment to runtime threat detection. Implement Pod Security Standards, RBAC, network policies, and NSA/CISA hardening guidance for production clusters.

Mac Python Setup Guide | Install and Configure Python Development Environment
Install Python, Xcode, Homebrew, and VS Code on macOS. Complete guide for setting up a professional Python development environment.
Managed Services
We help growing businesses strengthen security operations, respond faster to threats, and recover quickly—without hiring a full in‑house team.
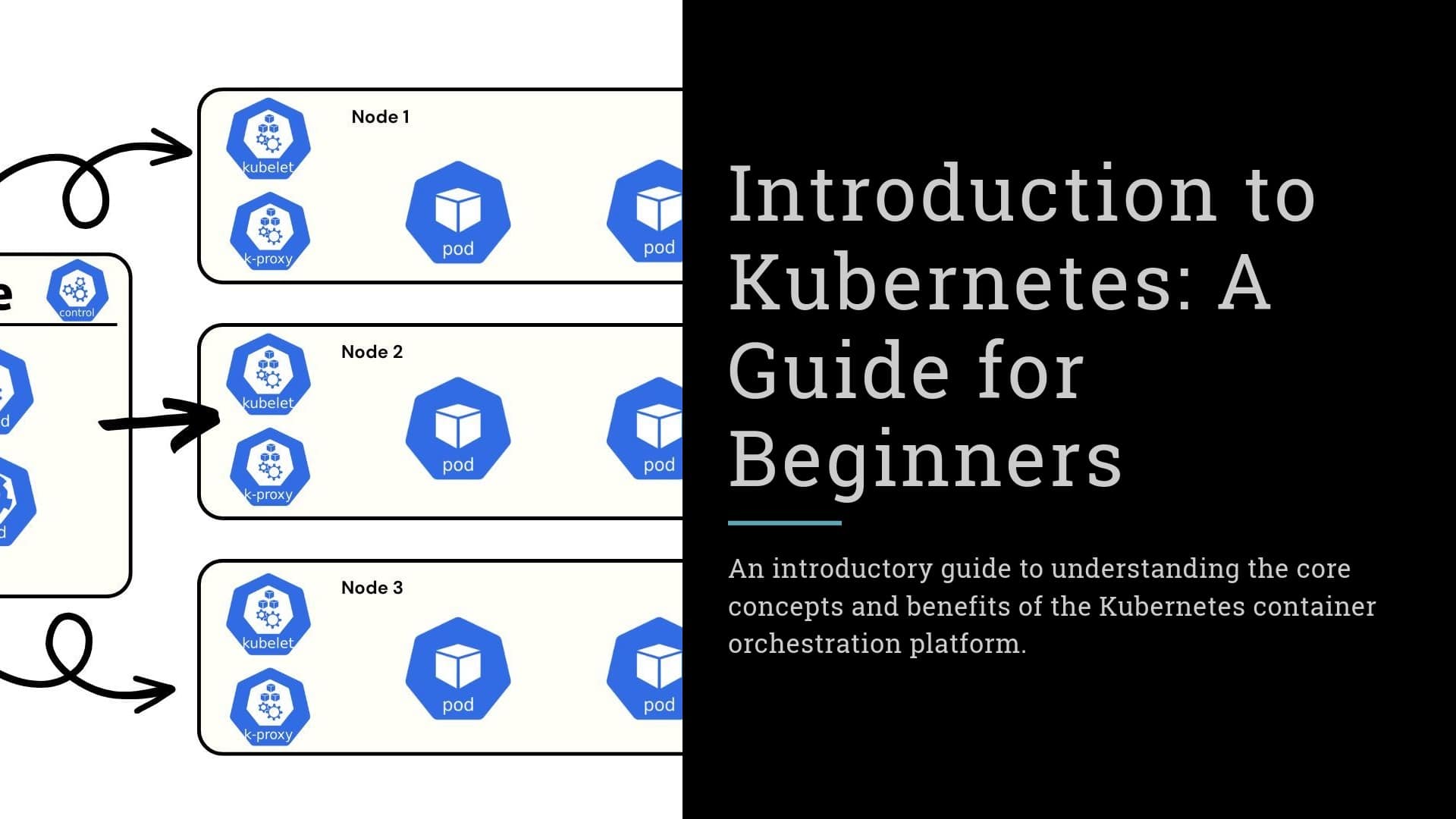
Kubernetes Container Orchestration | Master Guide
Learn how to deploy, scale, and manage containerized applications with confidence using industry-standard Kubernetes
MDR vs Traditional Monitoring | Expert Response
“We already have monitoring tools, so we don’t need MDR.”

NetApp Perfstat Analysis | 7-Mode Performance Guide
Master NetApp 7-mode perfstat analysis to troubleshoot CPU, disk, and network performance issues on your storage systems.
Multi-Cloud Cost Optimization Workflow
Master the complete 8-stage multi-cloud cost optimization workflow used by FinOps practitioners. Learn how to eliminate $44.5B in cloud waste through visibility, rightsizing, commitment planning, and continuous monitoring across AWS, Azure, and GCP.
NIST Compliance Services - CSF 2.0, SP 800-53, 800-171
We help businesses implement NIST CSF 1.1 and 2.0, NIST SP 800-53, NIST SP 800-171, NIST AI RMF, and NIST-SSDF to meet federal contract requirements, qualify for better insurance rates, and build resi...

NLP Stop Words Guide | Text Processing Optimization
Master stop words in NLP to improve processing efficiency while preserving meaning in your natural language processing projects.

Small Business Cyberattack Risk | Security Guide
Discover why small businesses are prime cyberattack targets and how MDR solutions provide enterprise-grade protection.
Python Try Except: Complete Error Handling Guide
Master Python exception handling with try, except, finally blocks. Learn best practices for robust error handling and debugging techniques.

OpenFiler Installation Guide | Complete Setup Tutorial
Learn to install OpenFiler 2.3 on virtual machines with proper storage configuration and web management setup
Page 13 of 64 • 959 articles total
Stay Ahead of Cyber Threats
Get expert cybersecurity insights, threat intelligence, and best practices to protect your business.