Cybersecurity Insights & Expert Guidance
Stay ahead of evolving threats with actionable cybersecurity insights, real-world case studies, and expert guidance from Inventive HQ's security team.
Featured Series
Ransomware-Proof Backup & Recovery | Acronis-Powered Protection
Not sure if your backups are truly ransomware-proof? Let’s review them together

Benefits of Using Virtualization for Disaster Recovery
Transform your disaster recovery strategy with virtualization. Reduce downtime, eliminate hardware dependencies, and ensure business continuity when disruptions strike.

Beyond WSUS: Modern Windows Update Management in 2025
Migrate from deprecated WSUS to Azure Update Manager, Intune, and Azure Arc. Complete guide for modern Windows patch management.

BigQuery vs. Redshift: Choose the Right Data Warehouse to Scale Your Business
Data warehousing has revolutionized how businesses handle massive volumes of data, enabling faster insights, strategic decision-making, and data-driven growth. Two industry leaders dominate this space...

Building a Classifier Using Python and Scikit-Learn

Case Study: Autoscaling for Black Friday Traffic Surges

Case Study: Cutting IT Costs by 38% with Cloud Migration

Case Study | How to do Cybersecurity Across a Distributed Organization | IHQ
Transforming Eight Healthcare Subsidiaries in Three Months

Case Study: Airline Cybersecurity Strengthening
From Active Breach to Robust Defense: A Comprehensive Cybersecurity Transformation
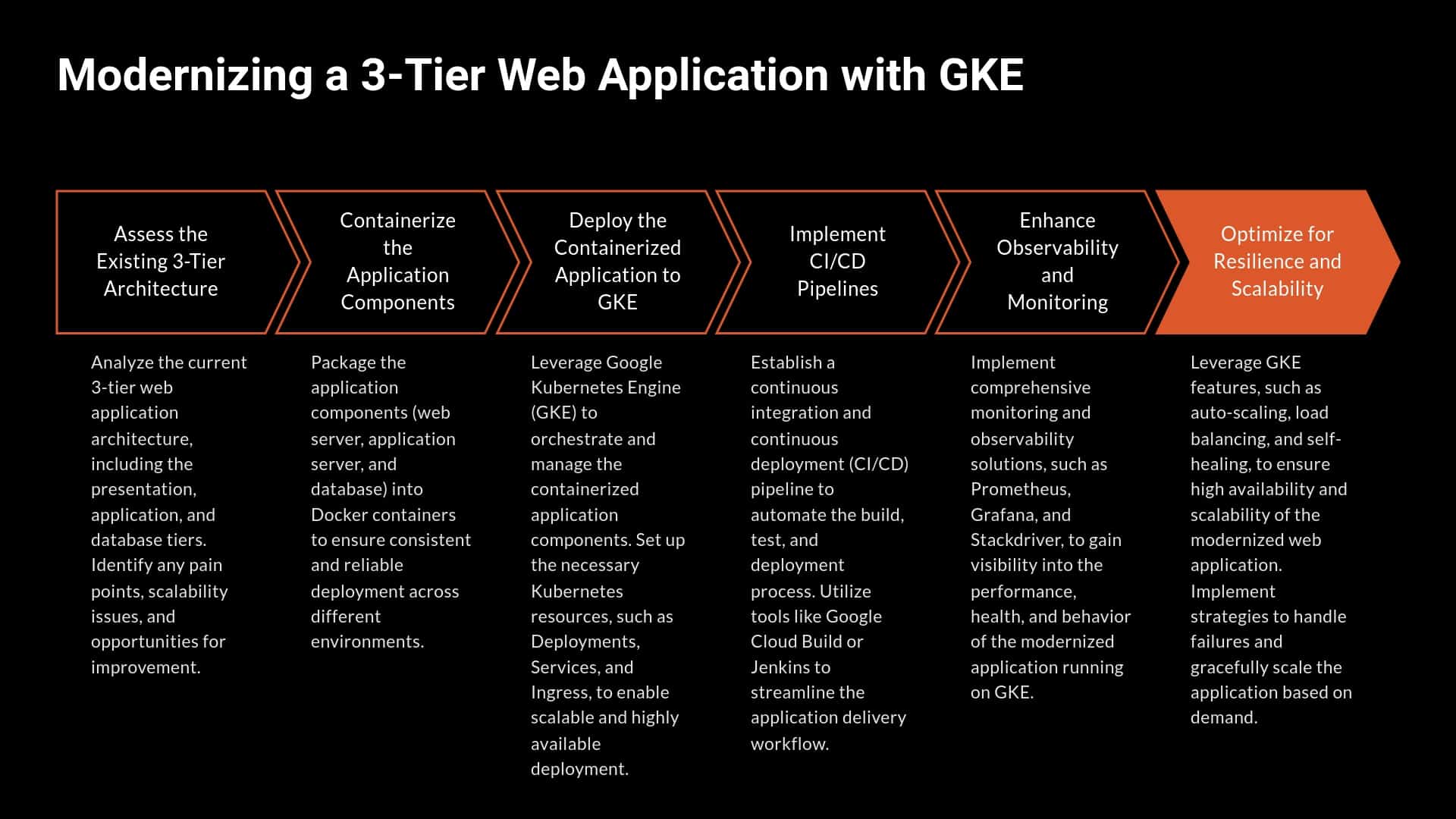
Case Study: Modernizing a 3-Tier Web Application with GKE

What Is a CDN? Content Delivery Network Guide
✅ Last Updated: January 29, 2025 • What a CDN is, how it works, pricing, providers, and setup steps

How to Install Chocolatey on Windows: Complete Setup Guide
Transform Windows software management with Chocolatey – your command-line package manager for seamless installations.

Choosing Between MDR, EDR, MSSP, XDR, and SOC: Complete Guide
In today’s rapidly evolving digital landscape, cyber threats are more sophisticated, frequent, and damaging than ever before. Businesses face everything from ransomware attacks and phishing schemes to...

Cloud Computing Beginners Guide | IaaS, PaaS, SaaS
Understanding modern computing: IaaS, PaaS, and SaaS solutions for flexibility, cost savings, and innovation

Cloud Console Login URLs: Complete Guide to AWS, Azure, GCP & More
Your comprehensive bookmark-worthy guide to accessing every major cloud provider console, with security best practices and multi-account management strategies for IT professionals.
Page 7 of 64 • 959 articles total
Stay Ahead of Cyber Threats
Get expert cybersecurity insights, threat intelligence, and best practices to protect your business.